The purpose of this tutorial is to know the importance of physical security and how to keep us safe from these kinds of Attacks. Spying to one's PC isn't a very big deal where they even can put the spy device on your motherboard silently, again…the importance of physical security. For indivisual's it might not be a big deal since you can carry your laptop or HDD where ever you go, but it's quite a big problem if it was a firm or office where they have a lot of important data on employees computer.
What Wikipedia says about Physical Security:
Physical security describes security measures that are designed to deny unauthorized access to facilities, equipment and resources, and to protect personnel and property from damage or harm (such as espionage, theft, or terrorist attacks).
Physical security we talked in this tutorial is part from Information Security where according to Wikipedia:
Information security, sometimes shortened to InfoSec, is the practice of defending information from unauthorized access, use, disclosure, disruption, modification, perusal, inspection, recording or destruction. It is a general term that can be used regardless of the form the data may take (electronic, physical, etc…)
What Wikipedia says about Physical Security:
Physical security describes security measures that are designed to deny unauthorized access to facilities, equipment and resources, and to protect personnel and property from damage or harm (such as espionage, theft, or terrorist attacks).
Physical security we talked in this tutorial is part from Information Security where according to Wikipedia:
Information security, sometimes shortened to InfoSec, is the practice of defending information from unauthorized access, use, disclosure, disruption, modification, perusal, inspection, recording or destruction. It is a general term that can be used regardless of the form the data may take (electronic, physical, etc…)
Remember: Do this at your own Risk and on your own computer/laptop, make sure you're not harming the others.
Requirements:
1. Kon Boot [Click Here to Download]
2. USB stick (the Kon Boot file size is about 5-6MB so you can calculate by yourselves)
Steps:
1. First, we will make the Bootable Kon Boot by using the default Kon-boot installer that already provided when we buy this program, but if we use the free version, we need to create the image ourselves. If you Don't know how to make a Bootable USB [Click Here] to See our Guide on How to create a Bootable USB.
Choose the USB we want to use to install kon-boot from the "available USB drives" drop down list and click "Install to USB stick" when finished.
The installation process will take approximately 1 minute.
Note: Make sure you choose the correct USB, because the installation process will erase all data on your USB device.
2. The Kon-boot USB now ready, we need to configure the BIOS settings to change the boot order to boot from USB. If you Don't know how to change Boot order in BIOS, Follow this Tutorial [Click Here].
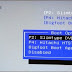
3. This is the preview when we successfully boot from Kon-boot USB.
4. After the Kon-boot initialization screen, it will normally boot the Windows. When we press the SHIFT key 5 times (sticky keys), we can see the command prompt pooped out with system role.
5. We can enter Windows without a password, just click the arrow and we already inside the system.
How to Prevent these types of Attacks:
1. Create a password for our computer BIOS.
2. Lock our computer physically to prevent someone open the computer case and reset the BIOS password.















0 comments:
Post a Comment